Openstack dashboard release IP for project/tenant
This took me couple of hours to figure it out in UI. Hence documenting:
To release floating IPs from a tenant or project of openstack.
- Login to dashboard
- Compute –> Access & Security –> Floating IPs
- You should can sort by Status (‘Down’)
- Select the ones with pt 3 and click on ‘Release Floating IPs’ button
- You should see that these floating IPs are released for other tenants to pickup.
CNI-Genie
The opensource project I’ve been actively working on. I took a video today on this.
Connecting two Open vSwitches to create a L2 connection between sites
Recently I played with Open vSwitch and it’s awesome! Open vSwitch is a multilayer virtual switch and it brings a lot of flexibility in the way you can create interfaces and bridges in Linux. It’s also a Linux distribution independent way to configure these things. Switching in software!
To create a bridge, simply run:
You can also create another bridge on top of it, to handle a VLAN for example:
Even better, create a bond based on LACP:
This is all quite nice but still basic. It gets interesting when you realise you can connect two switches like you can put a patch cable between physical switches. To test how cross platform this works, I setup two boxes: a CentOS 7 box and a Ubuntu 15.04 one. This shows it in a picture:
We’ll create a new bridge and add a vxlan interface that connects to the other vswitch. Then create a…
View original post 871 more words
Adding ssh-keygen manually
</pre> test@testenv:/# ssh-keygen -t rsa -b 4096 -C "karun.chennuri@test.com" Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: 90:b9:6d:84:9e:bc:71:80:19:12:ec:e4:5d:51:11:dc karun.chennuri@test.com The key's randomart image is: +--[ RSA 4096]----+ | .o.. .+++ | | o. +.+. E | | + .o.* . | | o .o B | | * S | | = | | . | | | | | +-----------------+ test@test-env:~$ ssh-add Could not open a connection to your authentication agent. # If you see above error then $ eval 'ssh-agent -s' SSH_AUTH_SOCK=/tmp/ssh-pxa9H7geUdOJ/agent.31326; export SSH_AUTH_SOCK; SSH_AGENT_PID=31327; export SSH_AGENT_PID; echo Agent pid 31327; $ SSH_AUTH_SOCK=/tmp/ssh-pxa9H7geUdOJ/agent.31326; export SSH_AUTH_SOCK; $ SSH_AGENT_PID=31327; export SSH_AGENT_PID; # Then again issue below command ssh-add this time it should work... test@testenv:/# ssh-add -l The agent has no identities. test@testenv:/# ssh-add Enter passphrase for /root/.ssh/id_rsa: Identity added: /root/.ssh/id_rsa (/root/.ssh/id_rsa) test@testenv:/# ssh-add -l 4096 90:b9:6d:84:9e:bc:71:80:19:12:ec:e4:5d:51:11:dc /root/.ssh/id_rsa (RSA)
VNCServer setup (Ubuntu desktop)
Steps to Install VNCServer on any VM
==========================================
ubuntu@karun-sec-4:~$ apt-get update ubuntu@karun-sec-4:~$ apt-get install -y gnome-core xfce4 xfce4-goodies vnc4server tightvncserver # If the folder .vnc not found, go ahead and create it manually & also xstartup file ubuntu@karun-sec-4:~$ vi ~/.vnc/xstartup def export XKL_XMODMAP_DISABLE=1 unset SESSION_MANAGER unset DBUS_SESSION_BUS_ADDRESS gnome-panel & gnome-settings-daemon & metacity & nautilus & gnome-terminal & startxfce4 & # If the folder .config not found, go ahead and create it manually ubuntu@karun-sec-4:~$ sudo chown -R ubuntu:ubuntu ~/.config #If gray screen sudo chown ubuntu:ubuntu ~/.vnc/xstartup chmod 755 ~/.vnc/xstartup reboot ubuntu@karun-sec-4:~$ vncserver -geometry 1920x1080 -depth 24 :1 # TightVNC client open and <ip address>::5901 password: <password> Now click on connect button #Note: to kill VNCserver ubuntu@karun-sec-4:~$ vncserver -kill :1
Steps to create a new Interface on Ubuntu 14.04 VM of Openstack
auto eth1 iface eth1 inet dhcp
2. sudo /etc/init.d/networking restart
3. On your instance select “Attach Interface” (In the popup chose a new network interface that you may’ve configured already)
4. Restart VM now, you should see your eth1 pick up an internal IP from the network.
My top security predictions for 2017
Ransomware: Malicious software designed to block access to the victim’s files until the victim pays a ransom in Bitcoin is a potential threat that we can see a rise in the next year. With the advent of cloud-based services, this is going to be increasingly common threat next year.
Data Loss/Leakage: Growing volumes of sensitive data in the cloud will invite hackers. Trust no one should be the principle to adopt. Strict Key Management Systems (KMS) should be adapted for data at rest and use Transport Layer Security for data in motion.
Mobile Malware: Facing this age old problem that always surfaces with a new face is quite a daunting task! At the enterprise level – effective antivirus products and malware defenses can combat malware to a larger extent. But the problem is with mobile devices joining the corporate internal wireless network are becoming soft targets! Attacks such as memory-resident malware is an emerging trend and forensically difficult to detect. Take a note of that!
IoT (Internet of Things): With the advent of Siri and Alexa, Privacy of individuals is undoubtedly a big challenge. This “always on” feature is a bit disturbing fact, though! Though security standpoint of this product is still unclear, but few experts say the product is secure with no obvious backdoors, however, only the times to come will decide the security posture of such products till hacked or especially in cases where software updates/patching flow-in opening the back doors. IoT is next big thing to lookup and a possible source of cyber attacks!
2017 Cyber Security Trends – 20 Professionals Speak Out
VeriClouds recently polled a field of Cyber Security professionals to get their opinions on the predominate threat trends in 2017. Our experts are CEO’s, CISOs, Engineers, Security Architects and Consultants working in universities, private consulting firms and corporations. Cyber Security 2017 Summary All responses, including those persons wishing to remain anonymous, were considered in writing […]
Source: 2017 Cyber Security Trends – 20 Professionals Speak Out
Limitations with Kubernetes Secrets
I’ve been working in Kubernetes space for quite some time now and ‘ve been coding in Go and directly contributing to this project in opensource world. Well coming to the subject of this blog, I would like to touch base here on a loosely designed object i.e. “secret store” in kubernetes. This topic has been a center of discussion in various forums, ‘am just trying to re-echo their voice in this blog.
Right now Kubernetes stores it’s secrets in etcd under /registry/secrets location. All the secrets are just base64 encoded and stored in etcd. This is what is the primary risk that security guys like me have been barking about. Now is there a way to get out of this issue? Yes but with a possible enhancement i.e. to externalize the secret store from Kubernetes system to something like HashiCorp’s HashiVault or Barbican coupled with Hardware Security Module (HSM).
Following are few risks adapting secret store mechanism in K8s:
- API server secret data is stored as plaintext (base64 encoded only) in etcd
- Secrets are shared if multiple replicas of etcd are run
- root on any node can read any secret from the api server
- User creating a pod that uses secret can also see the value of that secret
- No secret store access control at Kubernetes cluster level
- Key max length of 253 chars, Secret value <= 1MB. It is possible to accidentally push the Secrets definition to version control
Here is the change that ‘am looking for…It can be Barbican or HashiVault…
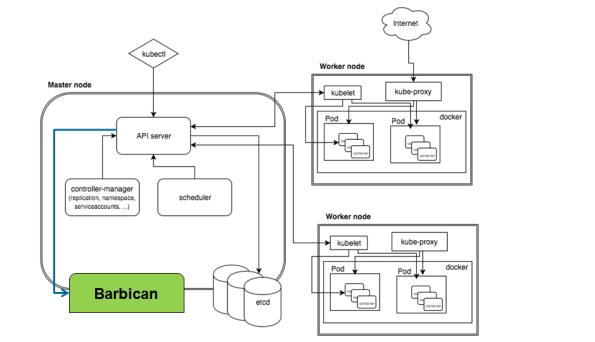
Currently there is no plug-in to K8S that can help externalize the secret store to Hashi Vault or Barbican. I developed one for both HashiVault and Barbican, I will upload the github link soon for it.

